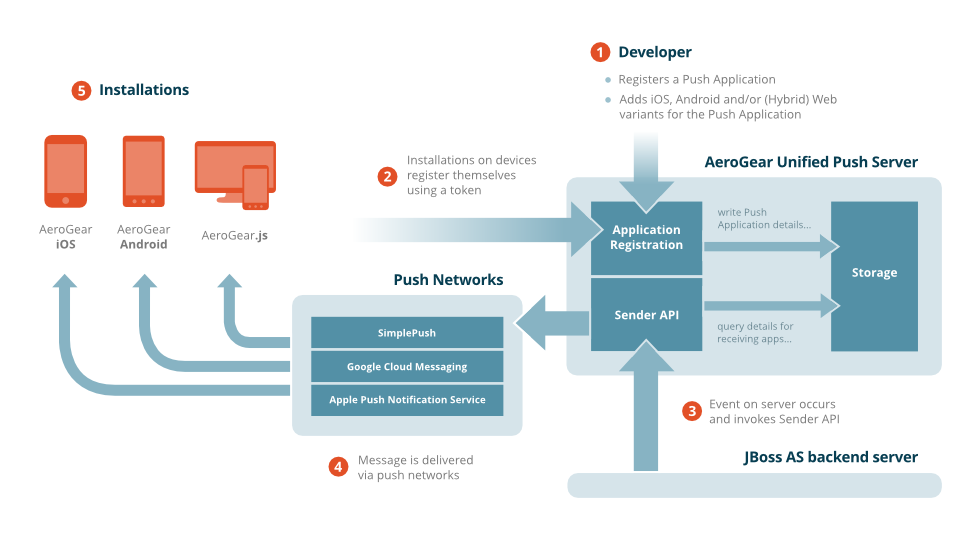
Our guest blogger this week is Albert T. Wong ([email protected])
The Payment Card Industry (PCI) Data Security Standard (DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including American Express, Discover Financial Services, JCB, MasterCard Worldwide and Visa International. The PCI Standard is mandated by the card brands and administered by the Payment Card Industry Security Standards Council.
The Payment Card Industry Data Security Standard (PCI DSS) was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent data security measures globally. PCI DSS provides a baseline of technical and operational requirements designed to protect account data. PCI DSS applies to all entities involved in payment card processing—including merchants, processors, acquirers, issuers, and service providers. PCI DSS also applies to all other entities that store, process or transmit cardholder data (CHD) and/or sensitive authentication data (SAD).
The PCI DSS Version 3.1 standard (released in 2015) lists twelve (12) requirements which retailers, online merchants, credit data processors, and other payment related businesses must implement to help protect cardholders and their data. The requirements include technology controls (such as data encryption, virus protection, end-user access control and activity monitoring) as well as required procedures.
Most of the requirements focus on site security and encryption, but some of them apply to securing your applications. The JBoss Enterprise Application Server (EAP) team has produced this technical overview document to assist you in understanding the PCI requirements, determining which requirements apply to JBoss Enterprise Application Server (EAP), and how JBoss Enterprise Application Server (EAP) implements the applicable requirements.
The use of JBoss Enterprise Application Server (EAP) in your electronic commerce site, even if installed and configured correctly, does not guarantee that your site will be PCI compliant. The purpose of this document is to describe the relationship between JBoss Enterprise Application Server (EAP) and the PCI Data Security Standard requirements, not about an entire operating environment. PCI compliance can also impose requirements on other components of your site involved in the storage, processing, or transmission of cardholder data, including firewalls, routers, Web servers, Operating Systems, databases and the web application. PCI compliance remains solely the responsibility of the merchant.
For your reference, here is the outline of the standard:
Build and Maintain a Secure Network
Requirement 1: Install and maintain a firewall configuration to protect cardholder data.
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters.
Protect Cardholder Data
Requirement 3: Protect stored cardholder data.
Requirement 4: Encrypt transmission of cardholder data across open, public networks.
Maintain a Vulnerability Management Program
Requirement 5: Protect all systems against malware and regularly update anti-virus software or programs.
Requirement 6: Develop and maintain secure systems and applications.
Implement Strong Access Control Measures
Requirement 7: Restrict access to cardholder data by business need to know.
Requirement 8: Identify and authenticate access to system components.
Requirement 9: Restrict physical access to cardholder data.
Regularly Monitor and Test Networks
Requirement 10: Track and monitor all access to network resources and cardholder data.
Requirement 11: Regularly test security systems and processes.
Maintain an Information Security Policy
Requirement 12: Maintain a policy that addresses information security for all personnel.
Where to find information about the Payment Card Industry (PCI) Data Security Standard
Payment Card Industry Data Security Standard:
https://www.pcisecuritystandards.org/index.shtml
JBoss Enterprise Application Server (EAP) and PCI compliance
The PCI Data Security Standard (DSS) addresses far more than the security of your JBoss Enterprise Application Server (EAP) application. It covers broad security requirements such as virus protection, and restricting physical access to cardholder data.
It is important to recognize the scope of the requirements, and which of them are related to JBoss Enterprise Application Server (EAP).
Control Objective
|
Relationship
|
1: Install and maintain a firewall configuration to protect cardholder data.
|
Related only to PCI DSS
|
2: Do not use vendor-supplied defaults for system passwords and other security parameters.
|
Focus area
|
3: Protect stored cardholder data.
|
Related only to PCI DSS
|
4: Encrypt transmission of cardholder data across open, public networks.
|
Focus area
|
5: Protect all systems against malware and regularly update anti-virus software or programs.
|
Related only to PCI DSS
|
6: Develop and maintain secure systems and applications.
|
Related only to PCI DSS
|
7: Restrict access to cardholder data by business need to know.
|
Focus area
|
8: Identify and authenticate access to system components.
|
Focus area
|
9: Restrict physical access to cardholder data.
|
Related only to PCI DSS
|
10: Track and monitor all access to network resources and cardholder data.
|
Focus area
|
11: Regularly test security systems and processes.
|
Related only to PCI DSS
|
12: Maintain a policy that addresses information security for all personnel.
|
Related only to PCI DSS
|
PIC Security Standards with Safe Online Casino Payments
Whether you enjoy online shopping, online sports betting or playing online casino games for real money, the most important thing is to feel safe while paying via the internet. There are lots of legal casinos that offer an excellent online service, and every professional gambler worldwide needs a secure online casino.
A useful method for online payment security is to create a casino account and make a deposit, and after that, you will have a short explanation of how the online payment is being processed in order to feel safe.
The website of Kenneth Peeples recommends you to use a different password to the ones you previously used, so you can protect yourself when opening an account at an online casino. Change your current password from time to time as well, and of course, look out on your bank statements.
PCI Security Standards Council Notices: Legal Terms and Conditions
Acceptance of a given payment application by the PCI Security Standards Council, LLC (PCI SSC) only applies to the specific version of that payment application that was reviewed by a PA-QSA and subsequently accepted by PCI SSC (the "Accepted Version"). If any aspect of a payment application or version thereof is different from that which was reviewed by the PA-QSA and accepted by PCI SSC – even if the different payment application or version (the "Alternate Version") conforms to the basic product description of the Accepted Version – then the Alternate Version should not be considered accepted by PCI SSC, nor promoted as accepted by PCI SSC.
No vendor or other third party may refer to a payment application as "PCI Approved" or "PCI SSC Approved", and no vendor or other third party may otherwise state or imply that PCI SSC has, in whole or part, accepted or approved any aspect of a vendor or its services or payment applications, except to the extent and subject to the terms and restrictions expressly set forth in a written agreement with PCI SSC, or in a PA-DSS letter of acceptance provided by PCI SSC. All other references to PCI SSC's approval or acceptance of a payment application or version thereof are strictly and actively prohibited by PCI SSC.
When granted, PCI SSC acceptance is provided to ensure certain security and operational characteristics important to the achievement of PCI SSC's goals, but such acceptance does not under any circumstances include or imply any endorsement or warranty regarding the payment application vendor or the functionality, quality, or performance of the payment application or any other product or service. PCI SSC does not warrant any products or services provided by third parties. PCI SSC acceptance does not, under any circumstances, include or imply any product warranties from PCI SSC, including, without limitation, any implied warranties of merchantability, fitness for purpose or non-infringement, all of which are expressly disclaimed by PCI SSC. All rights and remedies regarding products and services that have received acceptance from PCI SSC, shall be provided by the party providing such products or services, and not by PCI SSC or any payment brands.
Addressing the PCI Data Security Standard within JBoss Enterprise Application Server (EAP)
The following topics deal with each of the detailed requirements that pertain to JBoss Enterprise Application Server (EAP). Some of the requirements are directly related to the JBoss Enterprise Application Server (EAP) software package. Other requirements are unrelated, or indirectly relate to the JBoss Enterprise Application Server (EAP) software package. For example, indirect requirements can affect your use of the operating system security features to secure JBoss Enterprise Application Server (EAP) files.
PCI Assessment Services for JBoss Enterprise Application Server (EAP)
There is much more to navigating the PCI standard and the certification procedure than simply installing JBoss Enterprise Application Server (EAP) and making the adjustments we have outlined in the preceding sections. There are significant portions of the standard that, although it applies to your site, does not apply to the software application. To assist you in completely addressing these parts of the standard, Red Hat consulting can assist your site in becoming PCI compliant.
Addressing the PCI Data Security Standard within JBoss Enterprise Application Server (EAP)
The following topics deal with each of the detailed requirements that pertain to JBoss Enterprise Application Server (EAP). Some of the requirements are directly related to the JBoss Enterprise Application Server (EAP) software package. Other requirements are unrelated, or indirectly relate to the JBoss Enterprise Application Server (EAP) software package. For example, indirect requirements can affect your use of the operating system security features to secure JBoss Enterprise Application Server (EAP) files.
For several of the requirements that are related only to PCI compliance (and not to JBoss Enterprise Application Server (EAP)) you are referred directly to the PCI DSS for details. Ensure that you keep up with the rapid pace of changing security requirements.
Requirement 1: Install and maintain a firewall configuration to protect cardholder data
Many parts of requirement 1 such as your wireless network or router setup do not directly relate to JBoss Enterprise Application Server (EAP), but the requirements that relate to your site topology are extremely important. You must construct your JBoss Enterprise Application Server (EAP) site so that you never store cardholder data on internet-accessible systems. Additionally, JBoss Enterprise Application Server (EAP) sites should always use firewalls to separate themselves from the internet, internal networks, and any other system that is accessible to the internet. Ensure that you implement JBoss Enterprise Application Server (EAP) in a 3–tier configuration using the JBoss EAP Reference Architecture (http://www.redhat.com/en/resources/jboss-eap-6-clustering)
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters
Read the JBoss EAP Security Guide for details on changing the system password and system hardening.
Requirement 3: Protect stored cardholder data
Beyond the scope of JBoss EAP.
Requirement 4: Encrypt transmission of cardholder data across open, public networks
Disable SSLv2 and older security encryption on your web server.
Enable Federal Information Processing Standards publication 140-2 (FIPS 140-2) security standard.
Enable National Institute of Standards and Technology (NIST) Special Publications 800-131A (SP 800-131A) security standard.
Requirement 5: Protect all systems against malware and regularly update anti-virus software or programs
Although antivirus software is outside the scope of JBoss Enterprise Application Server (EAP), protecting your servers and network from malicious software should always be a priority for a responsible network administrator.
Requirement 6: Develop and maintain secure systems and applications
Ensure that your store error pages do not display stack traces, either visibly, or in the page source.
As your business needs change, you or your business partners might customize your JBoss Enterprise Application Server (EAP) site. As you do so, you must ensure that the customizations do not compromise your site security. Ensure that your developers understand the requirement to develop secure systems by referring to the PA-DSS and PCI-DSS.
Please also monitor the
top 10 list of security threats by the Open Web Appliction Security Project (OWASP)
Requirement 7: Restrict access to cardholder data by business need to know
Read the JBoss EAP Security Guide for details on access control lists.
Requirement 8: Identify and authenticate access to system components
Read the JBoss EAP Security Guide for details on default account policies.
Requirement 9: Restrict physical access to cardholder data
Beyond the scope of JBoss EAP.
Requirement 10: Track and monitor all access to network resources and cardholder data
Ensure that the correct level of logging is enabled. Please see JBoss EAP documentation for more details.
Requirement 11: Regularly test security systems and processes
Beyond the scope of JBoss EAP.
Requirement 12: Maintain a policy that addresses information security for all personnel
Beyond the scope of JBoss EAP.