Overview
Cojan van Ballegooijen, Red Hat Senior Solution Architect,
Bill Kemp, Red Hat Senior Solution Architect, and
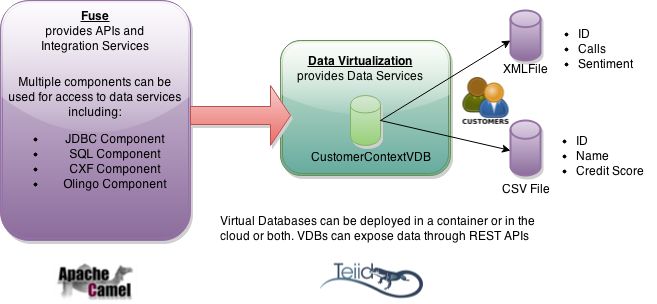
myself have created an example around a Customer Context Use Case to show how to use the Camel Components in Fuse to access a Data Virtualization Virtual Database (VDB). The data service provides the customer context which is aggregated data from a XML file and CSV file. The data on each customer provides the name, the credit score, the number of calls the customer has placed to customer support and the sentiment (Hot, Cold, Warm) toward the company from social media. We will review the components and show how to run the demo. The
demo repository is located in
jbossdemocentral on github. In our project directory we have the individual use cases which are built and deployed when running the scripts. The Teiid jdbc jar is loaded into the profile with wrap file during the run script.
Use Case 1 - JDBC Component
In the first use case we are set up the bean for the sql query that we want to execute and the bean for the datasource properties. A timer component runs a query every 60 seconds, the results from the query are then split into individual records and then sent to the log. We are using the Blueprint DSL in the blueprint.xml.
 |
| blueprint.xml design view |
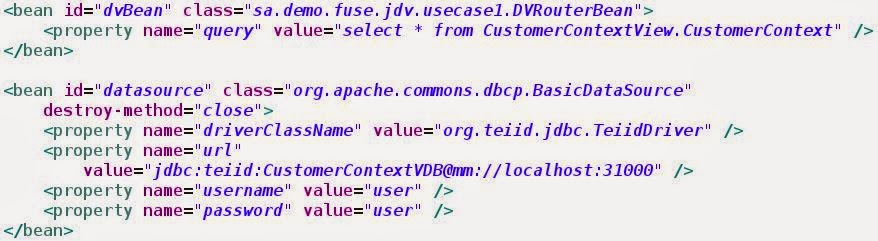 |
| blueprint.xml source view with the query property and datasource properties |
Note the url that accesses the CustomerContext Virtual Database. Also the query is set in the body and the datasource name is part of the jdbc URI.
JDBC Component excerpt from the Camel Component Page:
The jdbc component enables you to access databases through JDBC, where SQL queries (SELECT) and operations (INSERT, UPDATE, etc) are sent in the message body. This component uses the standard JDBC API, unlike the Camel
SQL Component component, which uses spring-jdbc.
Maven users will need to add thecamel-jdbc dependency to their pom.xml for this component. This component can only be used to define producer endpoints, which means that you cannot use the JDBC component in a from() statement. The URI Format for the JDBC component is:
jdbc:dataSourceName[?options]
This component only supports producer endpoints. You can append query options to the URI in the following format, ?option=value&option=value&...
Use Case 2 - SQL Component
The second use case is similar to the first in that a timer component runs a query every 60 seconds, the results from the query are then split into individual records and then sent to the log. Also we are using the Blueprint DSL in the blueprint.xml. The difference with the SQL component is the query is part of the URI of the component. Also we are loading the datasource into the SqlComponent class.
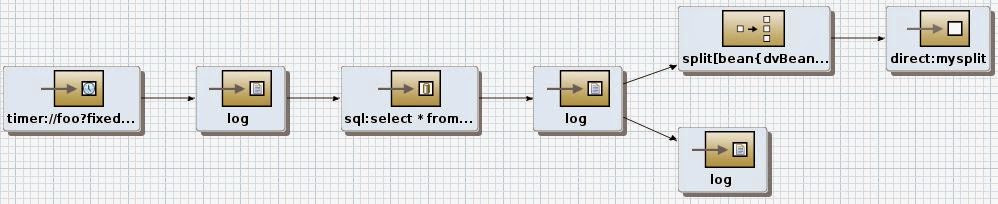 |
| blueprint.xml design view |
 |
| blueprint.xml source view of SqlComponent with datasource reference |
SQL Component excerpt from the Camel Component Page:
The sql: component allows you to work with databases using JDBC queries. The difference between this component and
JDBC component is that in case of SQL the query is a property of the endpoint and it uses message payload as parameters passed to the query. From Camel 2.11 onwards this component can create both consumer (e.g. from()) and producer endpoints (e.g. to()). In previous versions, it could only act as a producer.
This component uses spring-jdbc behind the scenes for the actual SQL handling. Maven users will need to add the camel-sql dependency to their pom.xml for this component. The SQL component also supports:
The SQL component uses the following endpoint URI notation:
sql:select * from table where id=# order by name[?options]
You can append query options to the URI in the following format, ?option=value&option=value&...
Use Case 3 - Olingo Component
Olingo Component excerpt from Camel Component Page:
The Olingo2 component utilizes
Apache Olingo version 2.0 APIs to interact with OData 2.0 and 3.0 compliant services. A number of popular commercial and enterprise vendors and products support the OData protocol. A sample list of supporting products can be found on the OData
website.
Maven users will need to add the camel-olingo2 dependency to their pom.xml for this component. The URI format for the Olingo component is:
olingo2://endpoint/?[options]
Use Case 4 - JETTY Component for a REST Service
For Use Case 4 we use a REST service to expose the OData Data Virtualization Service.
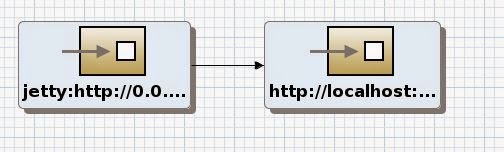 |
| blueprint.xml design view |
 |
| blueprint.xml source view of the route |
Note the CustomerContextVDB OData service is being used with the DV Username and Password as parameters. This returns all the data when accessing the Jetty URL, http://localhost:9000/usecase4.
The jetty component provides HTTP-based
endpoints for consuming and producing HTTP requests. That is, the Jetty component behaves as a simple Web server. Jetty can also be used as a http client which mean you can also use it with Camel as a producer.
Maven users will need to add the camel-jetty dependency to their pom.xml for this component. The URI format is:
jetty:http://hostname[:port][/resourceUri][?options]
You can append query options to the URI in the following format, ?option=value&option=value&...
Running the Project
Step 1:
Download and unzip the repository or
Clone the repository. If running on Windows, it is reccommended the project be extracted to a location near the root drive path due to limitations of length of file/path names.
Step 2: Add the DV and Fuse Products to the software directory. You can download them from the Customer Support Portal (CSP) or jboss.org.
Step 3: Run 'init.sh' or 'init.bat' to setup the environment locally. 'init.bat' must be run with Administrative privileges.
Step 4: Run 'run.sh' or 'run.bat' to start the servers, create the container and deploy the bundles.
Step 5: Sign onto the Fuse Management console, http://localhost:8181,
with the admin user and check the console log to see the output from the routes for the use cases. You can also view the Camel Diagrams. Browse to http://localhost:9000/usecase4 to see the data for Use Case 4 through Jetty.
The demo can be run in a docker container in addition to a local install. Full instructions can be found in
support/docker/README.md of the project.
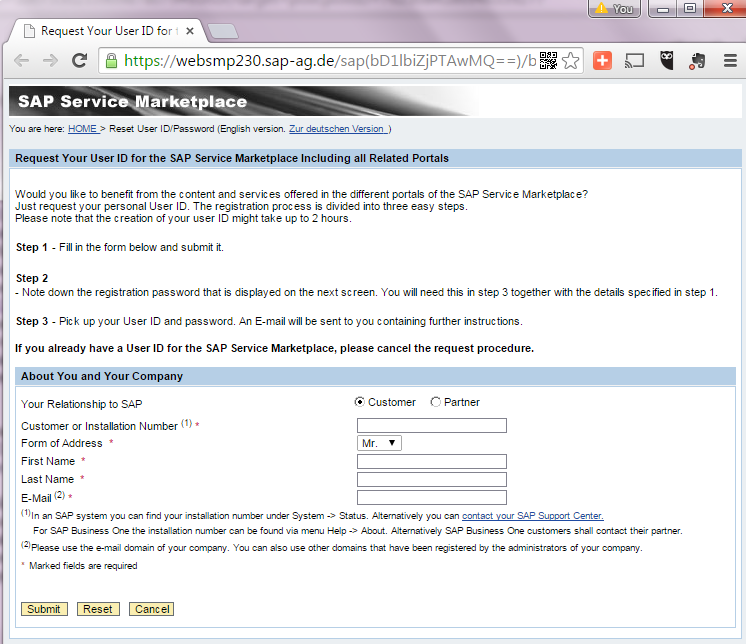 2. If you have no idea who the SAP administrator is for your company then you can register for an SAP S user ID by clicking the registration link in the upper right hand of SAP Service Marketplace home page or by following the link: http://service.sap.com/request-user. Please note that the customer or installation number is required for those who want to register as customer and a partner number is required for those who want to register as an SAP partner. In case you do not know customer or installation numbers that are required for option two, they can be requested through the SAP Customer Contact Us Page.
2. If you have no idea who the SAP administrator is for your company then you can register for an SAP S user ID by clicking the registration link in the upper right hand of SAP Service Marketplace home page or by following the link: http://service.sap.com/request-user. Please note that the customer or installation number is required for those who want to register as customer and a partner number is required for those who want to register as an SAP partner. In case you do not know customer or installation numbers that are required for option two, they can be requested through the SAP Customer Contact Us Page.








.png)